How Does Two-Factor Authentication Work will be described in this article. When was the last time you needed more than one password to access your accounts? That will soon be the past since two-factor authentication is replacing it in an effort to thwart hackers and strengthen account security online. Understand the benefits of using 2FA and how it operates. Next, to further help keep your personal data private, purchase a data-monitoring tool.
How Does Two-Factor Authentication Work In 2023
In this article, you can know about How Does Two-Factor Authentication Work here are the details below;
What is 2FA?
Two-factor authentication, sometimes referred to as dual authentication or 2FA, is a kind of multi-factor authentication (MFA) that uses two different ways to confirm your identity, hence increasing account security. Online, 2FA typically refers to an additional security layer that sits on top of a password.
Although 2FA’s two-step verification can occasionally feel like a bother, it’s essential for internet safety. In a world where personal information is frequently compromised, two-factor authentication (2FA) adds a major layer of security.
It can be difficult to pinpoint models of 2FA at times. A location or account may not be utilizing two-factor authentication just because accessing it involves two steps. A typical example of 2FA is using a bank card and a PIN number to take cash from an ATM. However, CAPTCHAs and security questions are not.
2FA vs. MFA 9multi-factor a authentication): What’s the difference?
MFA verifies your identity using two or more factors, which sets it apart from 2FA. It only uses two factors in 2FA. When a security door requires both an eye scan and an entrance card, for instance, the notion of multi-factor authentication also applies offline.
Multi-factor authentication may be used by companies, banks, and high-security offices for employee access. However, for most people and their online accounts, 2FA is secure enough.
Why do we need two-factor authentication (2FA)?
Because two-factor authentication is a more effective means to manage access than using a password to secure your personal information, we must implement it. Even if someone manages to breach a 2FA-protected account, they will still need the second access factor—such as your fingerprint or an SMS verification code—to gain access to your account.
Imagine if your password was all that was needed to gain access to your Facebook account. Your only defense against a pirate or cybercriminal looking to sell your personal data on dark web marketplaces without 2FA is a password.
The most advanced password cracking techniques utilized by hackers these days can’t be defeated by simple passwords. Passwords may be compromised in the thousands or even millions when data breaches happen. In response, businesses like Google and Facebook introduce 2FA to safeguard customer data.
Why then employ two-factor authentication? Because identity theft or having your personal information taken is far, far worse than just using a single password, even though it might take a little longer.
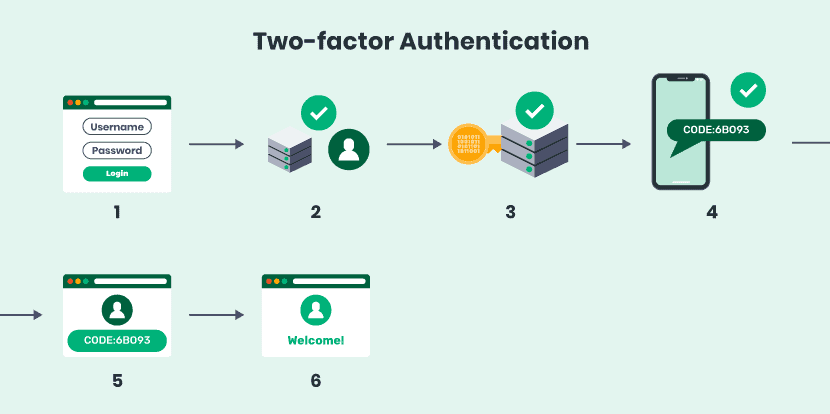
How does 2FA work?
In order to safeguard an account, two-factor identification uses two separate authentication techniques. In addition to your regular login and password, the second authentication method typically requires verification with a personal item, such your phone.
A password and security question login or access technique is not very secure since, if someone knows one password, they probably know the other or can figure it out. Because it’s considerably more difficult to gain access to a whole other factor—like your phone—two-factor authentication is far more secure.
The operation of two-factor authentication can be explained by three key factors.
2FA: The three factors
Something you have (like a bank card), something you know (like a password), and something you are (like facial ID) are the three factors that can be utilized for two-factor authentication. Two of these three elements are needed for 2FA. All three of these methods—or even GPS tracking—may be used by MFA to verify your exact position.
The three primary 2FA authentication factors are as follows:
· Knowledge factor
You are aware of this. Like a password or PIN code, it cannot be physically lost or found, but it can be copied.
· Possession Factor
This is something that, unlike a bank card or physical key, is difficult to copy yet is nonetheless susceptible to theft.
Inherence (biometric) factor
Unlike a fingerprint or facial ID, this is something that only you own and is difficult to counterfeit.
Two distinct factor types must be utilized in the two access methods for the authentication to be considered two-factor. Because a username and password are knowledge factors, using them together is not 2FA. Since a security question is also a knowledge factor, even one additional security question is ineligible for 2FA.
Knowledge, possession, or biometrics are the three distinct identifying factors that are used in two-factor authentication. Using two of the three factors—something you have (like a key), something you know (like a passcode), and something you are (like a fingerprint)—two-factor authentication confirms your identity.
Now consider your house key (possession element) and your garage door code (knowledge factor). You need both if you wish to use the garage to enter your locked home. This demonstrates two-factor authentication since it depends on both a key and a code that you possess. It will be difficult for you to enter that room without one of them.
Other typical instances of two-factor authentication include the following:
Taking out cash from an ATM
- You are aware of your PIN.
- Your bank card is with you.
Utilizing one-time SMS verification (OTP) tokens to access internet accounts
- You are aware of your password and username.
- You’ve got your phone.
Going abroad for vacation
- Your passport is with you.
- Verified via fingerprints, retinal scans, or facial recognition, you are who you say you are.
These illustrations highlight the need for two-factor authentication in order to improve personal security. A hacker could use 2FA to set up a keylogger and steal your password, but they couldn’t get past you if they didn’t have your phone, which is where the one-time verification code is transmitted.
The efficacy of two-factor authentication stems from the fact that its criteria remain constant in any given environment. The three fundamental 2FA characteristics of knowing, having, and being remain constant, and it is challenging to access more than one at once unless, of course, you are who you claim to be.
How to set up 2FA
While 2FA is available in many apps and services, it may not always be activated. To find out if 2FA is accessible, check the security settings of your account. Google creates 2FA codes automatically with its own software, Google Authenticator. Alternatively, you can use your Gmail or Google account to enable 2FA on your own. Also check Cybersecurity Software.
To enable 2FA on your Google Account, follow these steps:
- Open your Google Account and log in.
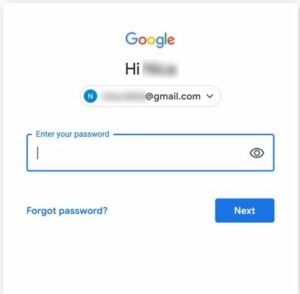
- To manage your Google account, click your profile picture.

- In the left panel, select Security and then 2-Step Verification.
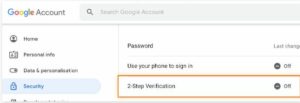
- In the Google account settings, highlight 2-Step Verification and click “Get Started.”
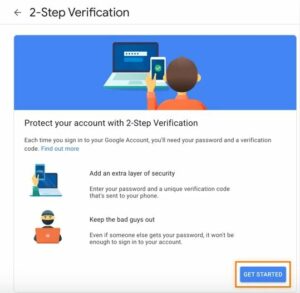
- Confirm your password by clicking “Get started” on the 2-Step Verification screen.
- Select the method you wish to use to confirm that your phone is actually yours: voice call, text message, security key, or prompt (default). Next, select “Try It Now.”
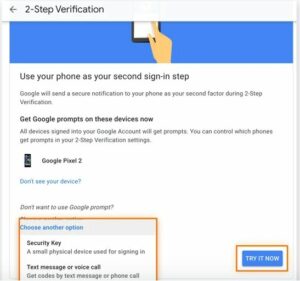
- Google’s 2-Step Verification website highlights more prompt possibilities and the “Try it now” button. Google will ask you to verify using the prompt on your phone.
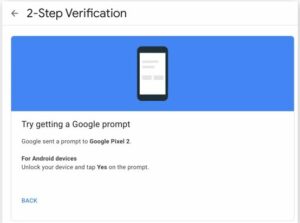
- The notification alerting you Your phone has received a prompt from Google.
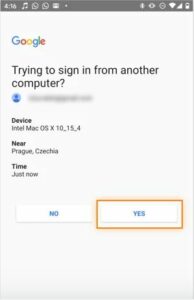
- Use your preferred authentication method to confirm.
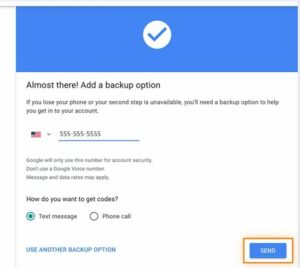
- In the event that you misplace your phone or are unable to validate the prompt, add a backup phone number or email. Next, select a message type (text or phone call) and press the Send button.
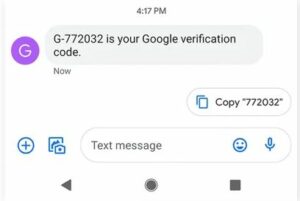
- When you click the “Send” button on the Google backup option for the 2-step verification page, a verification code will be shipped to your phone.
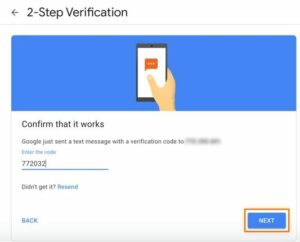
- Click Next after entering the Google Verification code in the 2FA settings for your Google Account.
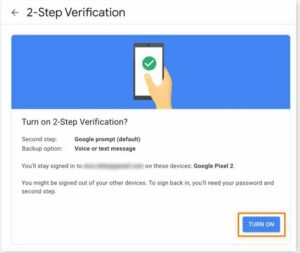
- “Turn on” option on the confirmation screen for Google’s two-step verification
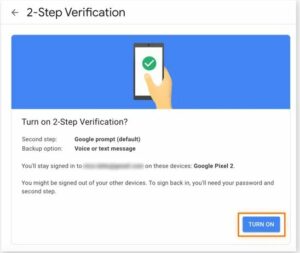
You’re through! Your Google Account is currently configured for two-factor authentication. Verify the Google email confirmation to be sure the procedure was successful. Also check Home Security System
In addition, you can set up 2FA on practically any app, platform, or device you use, including Facebook, Reddit, and your Apple device. A strong password with an additional verification mechanism combined with two-step authentication makes it significantly more safe than using only one password.
Is 2FA actually secure?
It is true that two-factor authentication is quite safe. While there is no 100% secure login solution, using 2FA increases your security against hacking attempts and data leaks. Once they discover that you have setup two-factor authentication, hackers will probably leave your account unharmed.
Since hackers are constantly learning, it’s possible that they will someday figure out 2FA. There are already message mirroring programs that can view your text messages. Furthermore, speech bots that steal 2FA codes are becoming a thing. In the event that all other methods are unsuccessful, hackers will still attempt to deceive users into divulging their 2FA codes through social engineering.
Are my passwords not secure enough anymore?
The security of single passwords has decreased over time. Hackers have a plethora of techniques at their disposal to break your passwords, including brute force assaults, keylogging, and password spraying. Strong, complicated passwords or passphrases are always a good idea, but they might not be sufficient to keep your accounts safe indefinitely.
To make it more difficult for hackers, you can use a random password generator if you don’t want to enable 2FA for every account you use. Additionally, keeping track of all of your strong passwords is made much simpler by putting them in one of the greatest password organizers.
But for all the accounts you need to maintain the safest and the ones you use the most, you should definitely utilize two-factor authentication.
Take data protection to the next level
While 2FA is a valuable security feature, you still need an excellent data-monitoring solution to safeguard all of your accounts. Avast Breachguard continuously searches the internet for data leaks and alerts you right away if any of your accounts are ever compromised.